I wrote a blog about this earlier but now I have a specific example that I think quite clearly demonstrates the difference between Autistic emotion and Neurotypical emotion.
I hope I am not burning any bridges by posting this, I will not share this on social media and almost no one reads this blog so hopefully it won’t be seen as offensive.
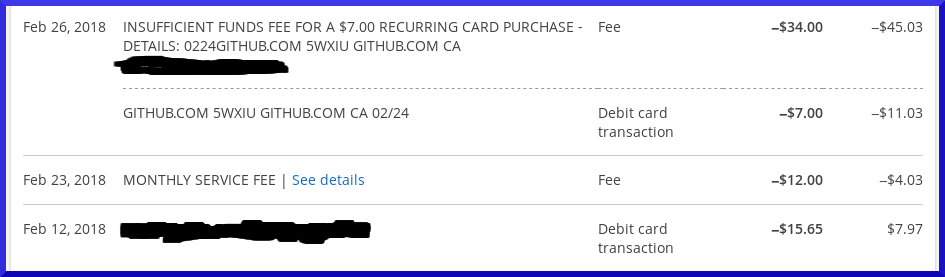
Recently a company I am a customer of, I have frequently in private expressed my frustration at the third party trackers that company has all over the websites it manages. I have expressed that concern for years. I do not like it.
I can block most of it myself with Privacy Badger but it bothers me that they are so willing to trade tracking information of their users in exchange for widgets on their sites. They should hire someone to write the widgets they need without trackers. Not me, their site is WordPress and I fucking hate the WordPress code base and even got kicked off their mailing list for calling some of their devs a bunch of fucking idiots (just for the record, I agree with getting kicked off the list for that, but I was also being truthful).
Yet here I am using a WordPress blog. My purpose is actually to expose myself to the user interface because I want to create something secure that users will use, and while I am good with code, I don’t understand what users want in an interface.
Anyway, Internet Tracking is a huge invasion of user privacy and the fact that it is so prevalent is a very serious issue for me. This company is one that especially should be concerned about the tracking of their users.
I love the company, I really do. For years, every time I share a link to their products and services it creates an internal conflict because in doing so, I am exposing other people who follow the links to the tracking that takes place as a result.
It may seem silly to the neurotypical people, but to me it is a very real problem and to a large extent I feel betrayed because on the surface, the company claims that privacy is important to them, they claim to provide high quality service, yet they continue to trade the privacy of their customers in exchange for free WordPress widgets instead of hiring a coder to create what they need that doesn’t track, or even finding free widgets that do not track.
My emotion that I frequently feel is that they are lying to me when they say my privacy matters to them, when they say the privacy of others matters to them, because I have informed them of the privacy violations taking place and they do not take action to change it.
From the song “Behind Blue Eyes” — ‘No one bites back as hard on their anger‘
For years I have been holding back on how upsetting it is for me for a company that is in an industry where privacy is important, for a company that claims that privacy is important to them, for a company that claims part of their higher than industry average fees is higher quality service, to allow their customers to be so blatantly tracked by third parties.
It has been a serious battle for me to hold back for as long as I have because it does feel like a betrayal to me. I know they do not intend it as a betrayal, but that is what it feels like whether it is intentional or not. And the only reason I have bitten back for so long is because I really really really like this company.
It is clear to me that either they do not care about why I feel that way, or they do not understand that I feel that way even though I have tried to express it in private. I choose to believe the latter because I do believe they are good people.
But not understanding my feelings doesn’t mean they aren’t real or that I do not have them, it just means they either do not know I feel that or do not comprehend why I feel that way. The feeling themselves are very real, but without understanding them, it is not possible for them to have empathy with those feelings. That’s an important concept.
-=-
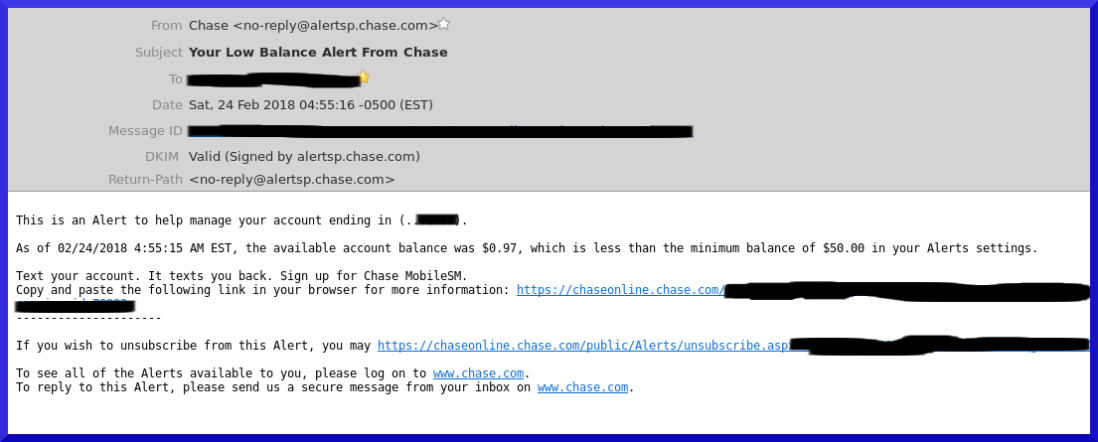
Two things happened that cracked my ability to continue my silence on the issue. First, I went to one of the websites run by this company and Privacy Badger reported an unusually high number of trackers on that page, I mean radically high. When I looked at what Privacy Badger was reporting, most of them were legitimate trackers and not false positives.
I then wrote a blog post on the issue. Since deleted, but I had to vent somewhere, because it really really bothered me.
A few days later, the Cambridge Data / Facebook misuse of tracking data broke.
That triggered some pretty strong emotions from me. Not because I was surprised, I knew this sort of thing was happening.
Basically when data about a person is collected without explicit informed consent, it will be abused. How can it not be abused when the person does not know how the data is to be used to even agree with what is being done with it?
Some people may not agree it is abuse, but whether tracked information can be used for a purpose is not the decision of those people, it is the decision of the person who tracked. Without their explicit permission, it is abuse. And often the abuse negatively impacts the person,.
The only way to collect data without explicit consent and not have the data not be abused is to completely anomymize the data in such a way as it is simply not possible to connects the dots from the data to the person.
It wasn’t that the data was being abused that bothered me, it is that I have been warning about this very thing for YEARS and people shrugged it aside and then suddenly when it is revealed my warnings were dead on, people were suddenly shocked and offended. Incidentally, Facebook is precisely one of the trackers I specifically warned about but was brushed aside as a loon for having concerns.
What that trigger did, I posted a screenshot from privacy badger of a website run by this company specifically showing that their sites include third party trackers from Facebook, and I tagged two of their blog administrators in the tweet.
That resulted in a response from the company, but not what I was looking for. What I was looking for was “We are working to fix this issue” but that is not what happened.
Keep in mind that notifying them in private is something I had tried numerous times in the past, and not just with them – with many companies. Publicly calling a company out over an issue the public is presently concerned with is often the only way to get action, which was my goal. My method at attaining that goal clearly failed, instead I think I pissed them off.
Clearly the approach I took was wrong. It caused emotional pain, I need to learn how not to do that. I acknowledge that, I own that. What is the right approach to get the trackers taken out of their site, I do not know, wish I could figure it out. They say they care about privacy so they can’t be adverse to removing them, I just don’t know how to get the action needed for their websites to match what they state.
Why is this is so important to me? Believe it or not, empathy!
Secret recordings show Cambridge Analytica would spread gay rumors to take down candidates
The same company that was misusing the private data from Facebook was involved in anti-gay bigotry as propaganda.
What happens when someone is exploring gender identity issues they do not want to have public, so they go to a website run by this company, and are tracked for visiting those sites – tracking that ties to their identity – and that tracking data ends up in the hands of someone like Cambridge Analytics that will use it for ill?
I do not want to see that happen.
-=-
The emotions this conveyed to me are real, I can not deny that. However, I do not understand them. Just like they do not understand my emotions. That makes it impossible for me to empathize with their emotions.
I was told that it “felt like a betrayal of trust” because they thought I was “part of the team”. That is their emotion, I just do not understand it.
First of all I do not know what it means to be considered “part of the team”.
I do not work for them, I am not their employee nor have I done any contract work for them.
Many years ago when I had a lot of money to spend with them, I wrote a WordPress plugin that anonymized Gravitar data collection – Gravitar takes an unsalted md5sum of an e-mail address which isn’t very secure, it becomes easy to determine if a particular e-mail address created a particular post reply. So I created a WordPress plugin that added a salt first to prevent that from happening. They ran it, so maybe that is what they meant by “part of the team” but that was so long ago and it appears they no longer use it. I’m guessing a WordPress plugin broke it, an Automattic employee once expressed that he did not like what my plugin did (Gravitar makes it cake for Automattic to track users) , I wouldn’t be surprised if code was put in specifically to break my plugin. I don’t know, I just would not be surprised.
I offered them a birthday calendar plugin, the company CEO said she would have the blog admin look at it but I could tell from the server logs no one ever accessed it, so my guess is they did not want it but just wanted to be nice about it, and I can both understand that and empathize with that.
I initially offered Naughty.Audio to this company and again they said they would look at it but it was clear to me they did not want it. So I run that myself.
I offered to recreate a stale site of theirs that full of bad links, but that also was something that ultimately they did not want.
I offered to create a solution to an audio problem that exists on one of their sites, and at that point since I was fucking broke and nearing eviction, I offered to do it for a price but I got no response at all.
I don’t see how I can possibly be considered part of any “team” or what they mean by that, but apparently they saw me as part of the “team”.
I certainly do not feel like any part of a “team”, especially when what I know are valid concerns about privacy and tracking are just brushed aside and it is suggested that it is something we just have to accept happens.
This may not be fair of me, but this is how I feel. I sometimes wonder if I’m actually seen as just an “Oh him again” except when it is convenient for them to see me as part of a “team.”
I do frequently share their links on Twitter and Tumblr. I do not do that because I am part of any “team” – I do that because I really like that company and feel loyalty to them. That loyalty to be honest is really waning. The things that are important to me do not seem to be important to them, and it seems I am treated much differently now that I am really poor. That last bit isn’t suggesting class discrimination, my own demeanor has changed since I have become poor and that could be why I am treated differently now. However regardless of the cause, the loyalty I feel to that company has been waning. But I still really like them.
It is possible to really like a company but not like one aspect of it, at least for me. Maybe for some people that is not possible.
The Republicans for example – they think it is impossible to like America but dislike many of the policies, and they call us America Haters when we speak out against the policies we do not like. I am not like them. I can really like something but still not like one or more aspect of it.
With respect to betraying trust, neither the blog post (now deleted) nor the tweet (now deleted) involved any information I was trusted with. Any random joe blow could have made the exact same post and tweet without any prior contact with the company, so I do not understand how it was a betrayal of trust.
But they clearly felt that way, and just because it does not make sense to me does not invalidate their feelings – which is why I deleted both the post and the tweet.
A quote I have seen many neurotypical people use:
An acquaintance merely enjoys your company, a fair-weather companion flatters when all is well, a true friend has your best interests at heart and the pluck to tell you what you need to hear. — E.A. Bucchianeri
That, or quotes like it, are commonly spread around but it seems that does not always apply and I can not figure out when it does and when it does not, this seems to be a case where it does not apply and I should not have had the pluck to tell them what they really need to hear yet so far really haven’t.
I was trying to be a true friend as it is so often defined and I do not understand the emotion it invoked.
Since I can not understand the emotion they felt, I can not empathize with it either.
And that is why autistic people often are seen as lacking empathy.
But it’s a two way street. They obviously don’t understand my emotion either and thus can not empathize with it.
Please remember that when hear people say autistic people lack empathy.
We don’t lack empathy, in fact we often have very strong empathy. But empathy simply is only possible when we understand the emotion.
And when you think we lack empathy, please understand we feel the same way quite often when our own emotions are not understood, when we are told our failures in society are our fault because we do not fit in to a world of people that are fundamentally and neurologically different than we are. That is something even many “autism experts” completely fail to understand and completely lack empathy for.
It is true that sometimes we do not understand the emotion of the neurotypical, but it is just as true that the neurotypical often does not understand our emotion.
Regardless I do not want to burn any bridges but the emotions I am building up over this are just too strong and I literally have no outlet. I can’t afford a therapist and my best friend is a PSO that I can not afford to call. I haven’t spoken to her since December. The only other people close to me always say the answer to problems are in the Bible, yet from what I read in the Bible, the answers it has they are politically opposed to. I literally have no one that I do not pay and right now I can pay, which means frustrations will come out in public and burn bridges even more.
So I have to stay away from that company, completely, or I will just make things even worse. Not my intent but that will be the result.
 Today on Twitter I saw the a tweet by Kay Marie showing a very seductive and enticingly beautiful image of Piper for a group blog she had written at Humiliation Bootcamp.
Today on Twitter I saw the a tweet by Kay Marie showing a very seductive and enticingly beautiful image of Piper for a group blog she had written at Humiliation Bootcamp.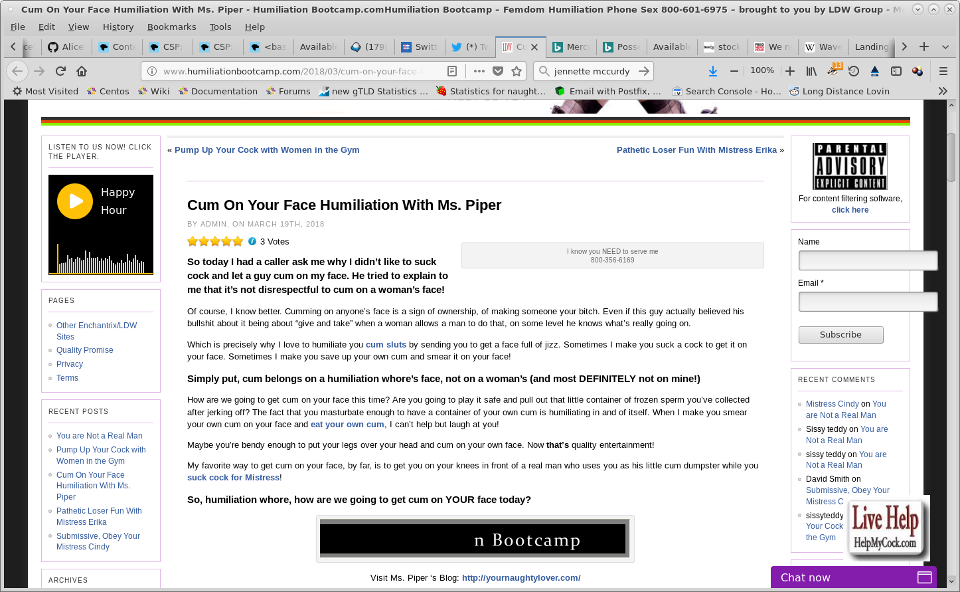
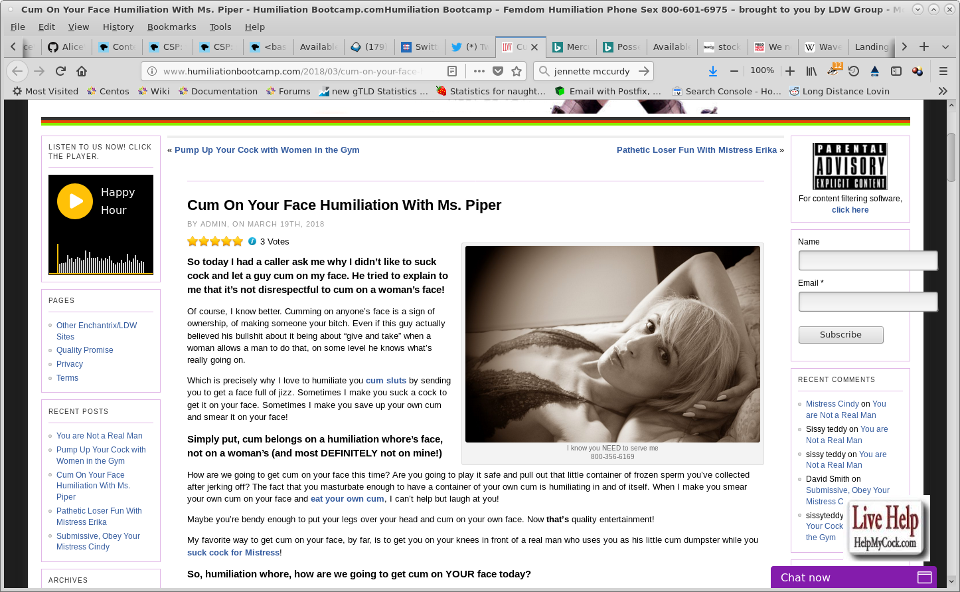


 As you can see, there is not much in it. There does not need to be much in it, the intent as I suspect is just to produce a “Like on Facebook” button.
As you can see, there is not much in it. There does not need to be much in it, the intent as I suspect is just to produce a “Like on Facebook” button.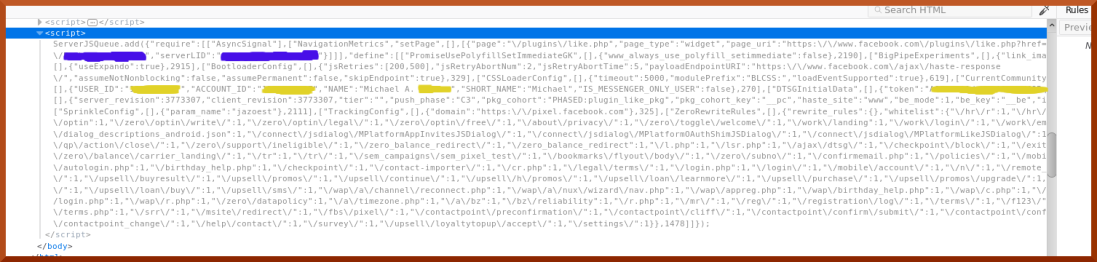 Again the blue blotches are to conceal the website this was on.
Again the blue blotches are to conceal the website this was on.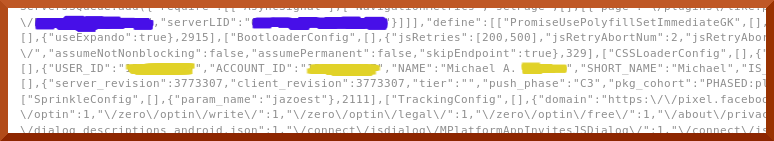





 This is my interface to the APCu cache engine. I made three major changes to my class to get it ready for public consumption.
This is my interface to the APCu cache engine. I made three major changes to my class to get it ready for public consumption.